一、接口方法:
public interface PlayerDao {
List<Player> findByName(@Param("playName") String playName);
}
Mapper文件1:
<select id="findByName" resultType="Player">
select *
from tb_player
where playName = #{playName}
</select>
Mapper文件2:
<select id="findByName" resultType="Player">
select *
from tb_player
where playName = '${playName}'
</select>
二、测试代码
关键代码如下:
public void testSqlInject() {
// 1.获取sqlSession
SqlSession sqlSession = sqlSessionFactory.openSession();
// 2.获取对应mapper
PlayerDao mapper = sqlSession.getMapper(PlayerDao.class);
String playName = "Lebron James";
String fakeName = "Lebron Jamesxxx' or '1 = 1 ";
//List<Player> list = mapper.findByName(playName);
List<Player> list = mapper.findByName(fakeName);
for (Player player: list) {
System.out.println(player);
}
System.out.println(list.size());
}
三、验证
验证#操作符
- 使用Mapper文件1:
- 执行testSqlInject,分别放开执行下面2行代码
List<Player> list = mapper.findByName(playName);
List<Player> list = mapper.findByName(fakeName);
执行第一行,只能找到一条记录,
执行第二行,不能找出任何记录,
从而验证了#的防sql注入。
验证$操作符
- 使用Mapper文件2
- 执行testSqlInject,分别放开执行下面2行代码
List<Player> list = mapper.findByName(playName);
List<Player> list = mapper.findByName(fakeName);
执行第一行,只能找到一条记录,
执行第二行,可以找出数据库的全部记录,
从而验证了$的sql注入的不安全性。
四、参考
Java 面试宝典是大明哥全力打造的 Java 精品面试题,它是一份靠谱、强大、详细、经典的 Java 后端面试宝典。它不仅仅只是一道道面试题,而是一套完整的 Java 知识体系,一套你 Java 知识点的扫盲贴。
它的内容包括:
- 大厂真题:Java 面试宝典里面的题目都是最近几年的高频的大厂面试真题。
- 原创内容:Java 面试宝典内容全部都是大明哥原创,内容全面且通俗易懂,回答部分可以直接作为面试回答内容。
- 持续更新:一次购买,永久有效。大明哥会持续更新 3+ 年,累计更新 1000+,宝典会不断迭代更新,保证最新、最全面。
- 覆盖全面:本宝典累计更新 1000+,从 Java 入门到 Java 架构的高频面试题,实现 360° 全覆盖。
- 不止面试:内容包含面试题解析、内容详解、知识扩展,它不仅仅只是一份面试题,更是一套完整的 Java 知识体系。
- 宝典详情:https://www.yuque.com/chenssy/sike-java/xvlo920axlp7sf4k
- 宝典总览:https://www.yuque.com/chenssy/sike-java/yogsehzntzgp4ly1
- 宝典进展:https://www.yuque.com/chenssy/sike-java/en9ned7loo47z5aw
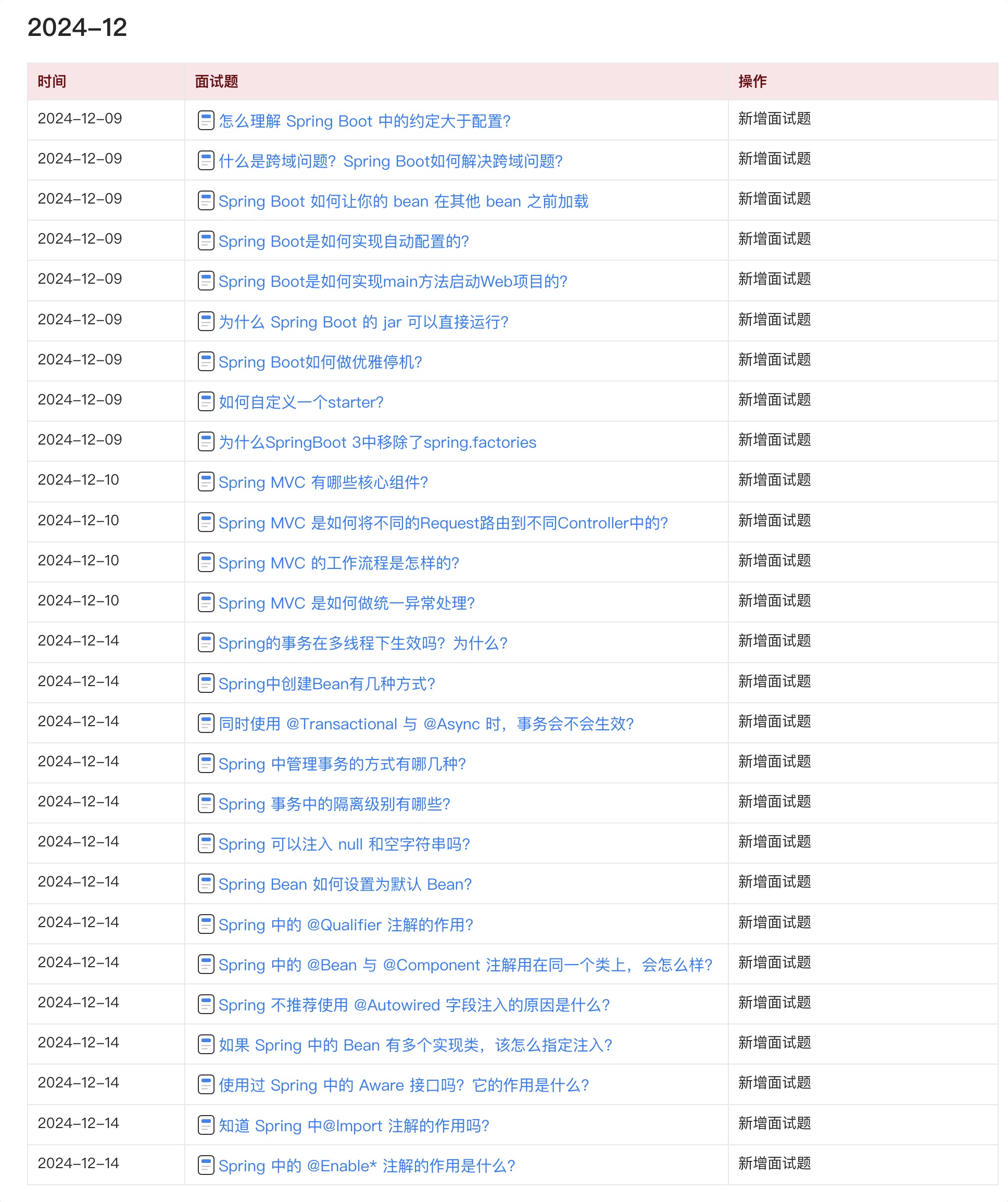
目前 Java 面试宝典累计更新 400+ 道,总字数 42w+。大明哥还在持续更新中,下图是大明哥在 2024-12 月份的更新情况:
想了解详情的小伙伴,扫描下面二维码加大明哥微信【daming091】咨询
同时,大明哥也整理一套目前市面最常见的热点面试题。微信搜[大明哥聊 Java]或扫描下方二维码关注大明哥的原创公众号[大明哥聊 Java] ,回复【面试题】 即可免费领取。